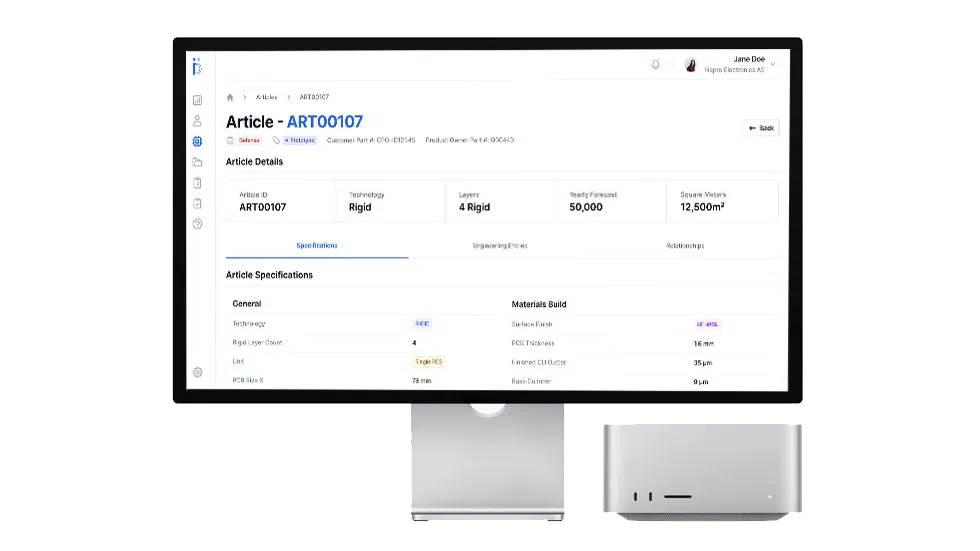
A proprietary developed IT system, setting the standard for the printed circuit industry. A platform that seamlessly integrates compliance, access control, and advanced cyber security measures
Design verification
Export control
Export controls are regulations limit export of some items. Every country has different regulations. It’s illegal to export in violation of these.
An item can be subject to export control depending on several factors, such as what it’s designed for or what capabilities it has.
The level of control, and possible export licences, also depend on the intended destinations and uses of the item.
A key purpose of export controls are to limit the ability of non-friendly countries to make use of advanced items and technology.
To achieve compliance with export control regulations, knowledge about products, components and technology must be combined with knowledge of regulations and other requirements
Supplier Audit
Cyber Security






Vision of ID
“Changing the industry can only be done by those who understand what the industry really lacks. Valuable solutions can only be provided when you care about the entire supply chain and understand that a digital system is more than efficiency and cost cutting
Robert Kurti, CTO
So what does our customers say about working with us?

In our domain which is mainly medical device, miniaturization and complex assembly, Design for Excellence is key.
Sylvain Joly
Electroniq R&D Team Manager, Valtronic
Working with Confidee is a real advantage, their expertise in handling EQs is unparalleled and their commitment to transparency regarding design and production improvements is commendable, that’s allowing to provide a high-quality service to our customer. Not only are they incredibly responsive, with a deep engineering knowledge, but they also add a personal touch that makes every interaction feel tailored to our needs. It’s this combination of efficiency and personalized service that keeps us coming back to Confidee time and time again

I’m thrilled to work with Confidee. Our goal is quality, efficiency and up-to-date technology, Confidee is the perfect PCB partner, fulfilling all our needs.
Harri Kaivos
Product Director, Xortec
They pioneer the industry with their extensive experience, focus on compliance and state of the art IT system. Their robust values, anchored in transparency, honesty, and personalized interactions, match perfectly with our business approach and connect well with our customers. An exceptional responsiveness to RFQs and unwavering commitment to top-notch technical support and flexibility, set them apart
Need to understand how ID works?